Advance the spam detection capabilities of your low-cost web application firewall (WAF) by integrating Apache .htaccess with Project Honey Pot. This post describes a combination of techniques using both of these tools to reduce spam traffic hitting your website.
Project Honey Pot is a tool for identifying spammers and spambots targeting your website. One off-label use for Project Honey Pot is integrating it with .htaccess to create a combined low cost web application firewall and honeypot solution.
Webmasters interested in participating in Project Honey Pot are required to register and then upload a Project Honey Pot provided spam trap webpage to their web server. After installing the Project Honey Pot software, .htaccess is used to point spammers to your honeypot. Additionally, many popular content management systems such as WordPress, Joomla, and Drupal have plug-ins that can be configured to use Project Honey Pot's spam blacklist. Combining your honeypot with the blacklist will further enhance your ability to stop spammers and spambots visiting your website.
For websites that already have a Web Application Firewall through a Content Distribution Network, the .htaccess can be used to supplement or increase the level of security provided by the CND WAF. The below diagram details the reference architecture.
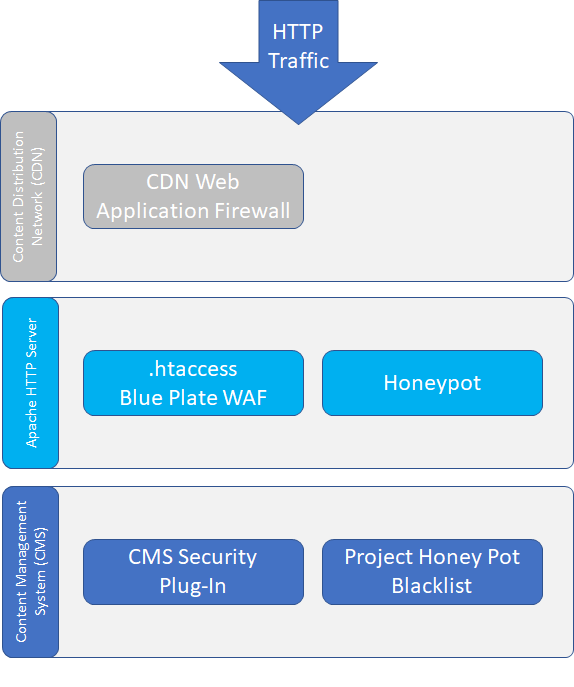
Creating Your First Spam Trap With .htaccess
To get started, register and install the Project Honey Pot software on your website following their instructions. Once installed you will have a unique webpage file name that serves as your honeypot.
Creating your first spam trap using .htaccess is easy and we will start with the previous .htaccess file we created in the last blog. Our previous file looks like this:
|
### =================== Blue-plate Special Firewall =================== ### ### !!!!!! Always Backup Your Previous Unmodified .htaccess File !!!!!! ### !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! ### ### =================== Blue-plate Special Firewall ===================
##### RewriteEngine enabled - BEGIN RewriteEngine On ##### RewriteEngine enabled - END
##### RewriteBase set - BEGIN RewriteBase / ##### RewriteBase set - END
##### Block directory browsing -- BEGIN IndexIgnore * Options -Indexes ##### Block directory browsing -- END
|
The code for your first spam trap starts after the last line of the previously created file. For this blog, we will use the filename "honeypot.php" to refer to the honeypot file installed from Project Honey Pot.
To catch potential spammers, we are going to examine the USER_AGENT variable that HTTP traffic is sending your website. The command RewriteCond will be used in conjunction with RewriteRule to test a condition and execute an action on your web server using the .htaccesss file.
We will test USER_AGENT using RewriteCond for common strings that spam bots have included in their USER_AGENT variable. The strings to be tested include “Wget”, “curl”, and “apache”. If our test is positive, the command RewriteRule forwards the tested HTTP traffic to the honeypot for evaluation by Project Honey Pot.
It is critical to ensure that the HTTP traffic is not the traffic that was already tested and redirected to the honeypot. To test this, we will use the command RewriteRule on the REQUEST_URI variable.
The .htaccess code to perform USER_AGENT string evaluations for “Wget”, “curl”, and “apache” and forward positive tests to the honeypot is listed below:
|
##### Redirect Linux Programs/Commands Used By Hackers and Spammers To Honeypot -- START RewriteCond %{REQUEST_URI} ! honeypot.php/ RewriteCond %{HTTP_USER_AGENT} ^.*Wget* [NC,OR] RewriteCond %{HTTP_USER_AGENT} ^.*curl* [NC,OR] RewriteCond %{HTTP_USER_AGENT} ^.*apache* [NC] RewriteRule ^(.*)$ /honeypot.php/ [NC,L] ##### Redirect Linux Programs/Commands Used By Hackers and Spammers To Honeypot -- END
|
The working file is available for download here. We welcome questions, comments, and thoughts on these techniques, reach out to the PCCS Labs Team at
