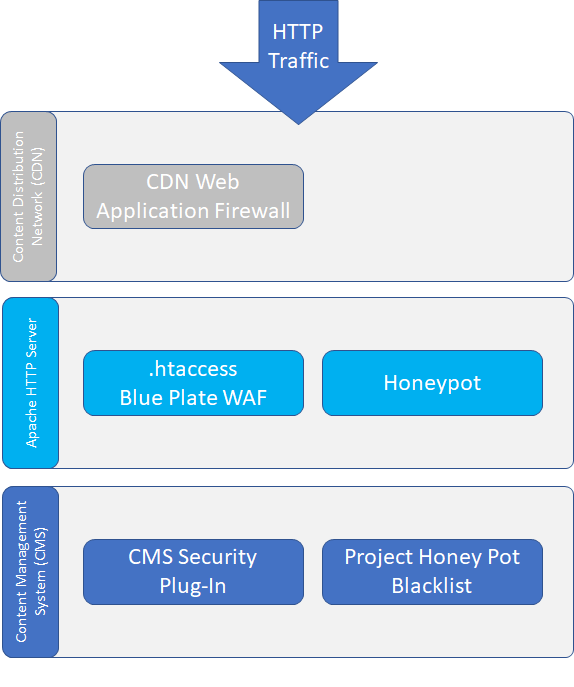
At PCCS labs we have access to sophisticated machine learning and artificial intelligence based cybersecurity tools. These tools are costly and the cyber risk may not warrant the cost of such tools for many small organizations. This blog details how to use Apache's .htaccess file to implement a low-cost Web Application Firewall (WAF) and is part of our effort to pass along cybersecurity knowledge to help secure the greater community.
Security is a unique challenge for cost-conscious websites that need to address a specific threat, spam annoyance, or risk but lack the resources to implement security tools such as a Web Application Firewall (WAF). Basic web hosting plans that many small organizations use typically do not include web security tools as the hosting company handles security. Many of these basic web hosting plans focus on content management systems such as WordPress, Joomla, and Drupal. One tool that most Apache-based web hosts do allow customers to use is the .htaccess file.
Using .htaccess does affect the performance of your Apache HTTP Server, and you should monitor response times when using this tool. If your hosting plan allows access to the httpd config file or ModSecurity those are the preferred methods for these techniques but most basic web hosts do not authorize customers to access these tools. The .htaccessfile can also be used in alongside content distribution network (CDN) web application firewalls (WAF) such as CloudFlare, Imperva, and Incapsula to further customize and strengthen your web security.
In this blog, we discuss methods that can be implemented using the .htaccess file to assist in the mitigation of troublesome web traffic. When implementing and testing these methods, it is critically important to keep a backup of your .htaccess file before any modification, and you must have an understanding of how to revert to this backup in the event your modifications cause errors.
Keep in mind that this blog is only covering one web security tool and you should have a comprehensive defense in depth cybersecurity strategy based on risk to ensure your digital presence is secure.
Getting Started With .htaccess
The .htaccess file typically is located in the web root directory of your host file system. Commonly the web root directory is named “www” or “public_html,” consult your hosting provider if you are not sure where to locate the file in your specific host configuration. Most Apache web hosting plans include a tool called cPanel or Plesk in which you can access a file browser to find your .htaccess file and more advanced users may prefer to use SSH.
Some host configurations may not have a .htaccess file setup in the root web directory by default, in this case, create a text file named .htaccess and save it in your root web directory.
Once you have found or created your .htaccess file, make two copies of this file, the first is a backup of the original unmodified file, this blog will use the name ”htaccess_backup_[date]” and the second is the version you are going to modify, this blog will use “htaccess_[date]_[version]”. The next step is to open the second file version of the ”.htaccess” file in your favorite text editor, this blog will use Notepad++ as the text editor.
To get started in using .htaccess, we first add comments in the .htaccess file. Comments are represented using “#” symbol. It is a best practice to start a .htaccess file with a comments section, below is the comment header we will use to start our .htaccess file.
|
### ================ Blue-plate Special Firewall ====================== ### ### !!!!!!!!!!!!!!!!!!!! Always Backup Your Previous Unmodified .htaccess File !!!!!!!!!!!!!!!!!!!!!! ### !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! ### ### ================ Blue-plate Special Firewall ======================
|
Save your edited file after adding the above comments and upload it to your website’s web root directory. Don’t change the file name to .htaccess yet, keep it in your selected file name format (we are using “htaccess_[date]_[version]”). After your upload is complete, you will activate the file on your server by replacing your current .htaccess with the newly uploaded version.
Users have found the best way to do this is to use the copy command, by copying your new version (we are using "htaccess_[date]_[version]") to .htaccess and overwriting the current .htaccess file. Alternately you can delete your current .htaccess and then rename your uploaded file to .htaccess but this will lead to a small point of time that your web server is left unprotected by .htaccess. After replacing your previous .htaccess file, visit your website to ensure everything is working correctly.
The next couple of commends that we are going to add to the .htaccess file will turn on Apache features that will be used later on in this blog.
After your initial comment header, add the below commands to your modified .htaccess file (we are using “htaccess_[date]_[version]”). To understand these Apache features further, read the Apache Web Server documentation, or google the command to read one of the many tutorials written about them.
|
#### RewriteEngine enabled - BEGIN RewriteEngine On ##### RewriteEngine enabled - END
##### RewriteBase set - BEGIN RewriteBase / ##### RewriteBase set – END
|
Finally, we will enable our first critical security feature using the .htacceess file, which will prevent file browsing from public web browsers of your web server directories. To accomplish this, add the following code to your file and follow the previous file copy process to enable it on your web server.
|
##### Block directory browsing -- BEGIN IndexIgnore * Options -Indexes ##### Block directory browsing -- END
|
The working file is available for download here. We welcome questions, comments, and thoughts on these techniques, reach out to the PCCS Labs Team at